Mapping Compliance Packages
Mapping similar Compliance Packages
Introduction
As explained in our Problem & Solution approach to GRC, eramba links problems (in the case of Compliance Management, we refer to Compliance Requirements) with Solutions (Internal Controls, Policies, Projects and Exceptions).
Some practitioners want to link compliance requirements in between different packages as well as linking to solutions. In this episode, we clarify how mappings work and how they are implemented in eramba.
Mapping Logic
Sometimes requirements from different publishers (PCI, ISO, NIST, etc.) are similar and they can be considered to be equal. In this case, you can instruct eramba to synchronise any treatments you have (Internal Controls, Policies, Projects, etc.) between those requirements you consider to be the same.
For example:
- You may consider that PCI 2.3.5 is similar to PCI 2.3.6, HIPAA 5.4 and 800-53 item 1.4.b.
- Your Internal Control “AD Security Standards” that you have been using for PCI 2.3.5 can be used as well for the other three requirements.
- If you create the mappings above, the internal control "AD security standards" will be automatically linked to the compliance requirements PCI 2.3.6, HIPAA 5.4 and 800-53 item 1.4.b.
The following fields are synchronized from the origin to the destination compliance items:
- Internal Controls
- Policy Management
- Compliance Exceptions
- Asset Risk
- Third Party Risks
- Business Continuity Plans
- Assets
Note: You can not define which fields will be synchronised.
Once mappings have been defined the compliance analysis module (Compliance Management / Compliance Analysis) can be used to edit an item. If the item has mappings defined you will notice a warning on the fields:
Whatever changes are made to these fields will be copied to all mapped items. You can see what items are mapped on the “Mappings” tab.
On the Compliance Analysis module, you might want to see what items are mapped as soon as you list compliance items. For that you will need to change the filter and enable the mappings field to be displayed on the default filter.
If any item is mapped to other items it will then be visible in the new column on the filter.
Note that a mapping is defined by telling eramba which is the origin and the destination (multiple) items. This means that whatever treatment (policies, controls, etc) are defined on the origin will be copied automatically to the destination. Since the destination is being synchronised with the origin, you won't be able to edit the fields on the destination item once a mapping has been defined.
Note this is an enterprise feature.
Manual Mapping
Before you can begin using this feature you will need to have at least one compliance package uploaded using the Compliance Management / Compliance Packages module. In that same module, the Compliance Mapping tab is the one you will use to define your mappings.
Creating mappings is simply telling eramba which compliance package item (just one) is related to which other items (more than one). In the scenario described above you will need to define three mappings.
|
Source |
Destination |
|
PCI 2.3.5 |
PCI 2.3.6 |
|
PCI 2.3.5 |
HIPAA 5.4 |
|
PCI 2.3.5 |
HIPAA 1.4.B |
By clicking on Actions / Add you can define each one of these mappings.
You will define the origin and destination of the mapping. Remember anything defined on the origin (controls, policies, etc) will be copied to the destinations automatically.
As you define your mappings, they will be shown on the filter below. At any point in time you can edit or delete these mappings.
If you create a map for PCI 3.4.5 (assume it already has some treatment defined, such as Internal Controls, Policies, etc.) to ISO 5.6.7 - as soon as you save the new mapping the synchronisation will take place and whatever PCI 3.4.5 has will be copied to ISO 5.6.7. You won't be able to edit the mitigation fields on ISO 5.6.7 as they are inherited from the PCI requirements.
If you delete an existing mapping the treatment for the items involved will not change. Everything will stay as it was before the deletion took place.
If you edit a mapping, those new items included will be synchronised automatically. Items removed will be left as they were before the change took place.
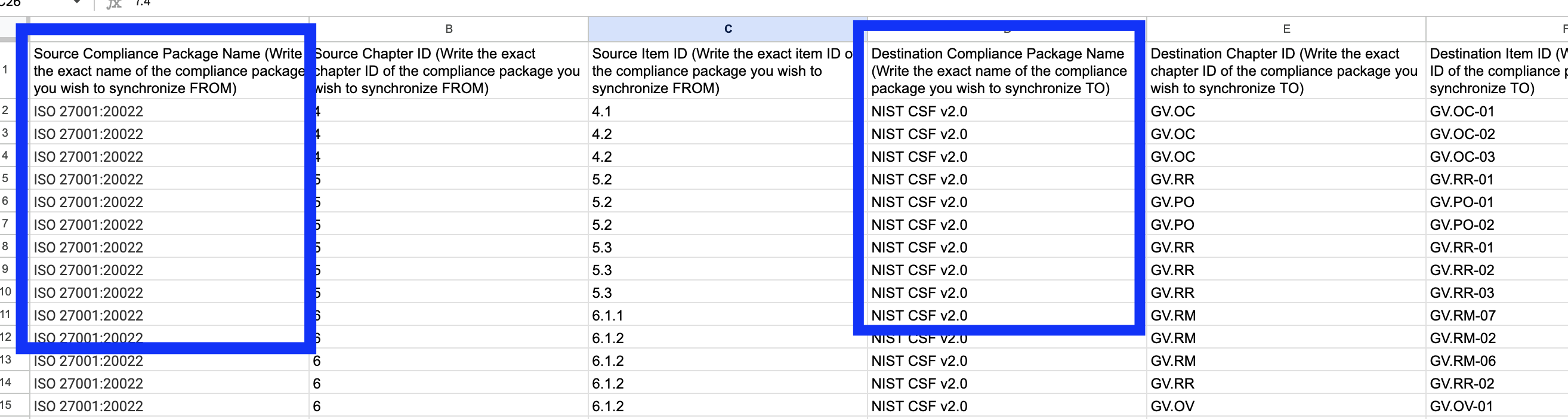
CSV Imports Mapping
The same task described above can be achieved using CSV files. The CSV template can be downloaded from the Actions / Import / Download Template. It must be completed according to the instructions provided on the CSV template file.
Mapping Database
In the table below you can find a database of mappings that will automatically work if you have used our compliance packages. These mappings can work in both directions, you just need to switch the "Source" for the "Destination".
The table below has the list of available mappings:
| Source Compliance Package | Destination Compliance Package | Download |
|---|---|---|
|
ISO 27001:2022 |
NIST CyberSecurity Framework v2 |
|
|
ISO 27002:2022 |
NIST CIS Controls v8 |
|
|
ISO 27001:2022 |
PCI-DSS V4 |
|
|
ISO 27002:2022 |
NIST CyberSecurity Framework v2 |
|
| ISO 27001:2022 | NIST 800-53 Rev. 5 | Download |
|
ISO 27001:2022 |
Digital Operational Resilience Act (DORA) |
|
|
ISO 27002:2022 |
Digital Operational Resilience Act (DORA) |
|
|
ISO 27001:2022 |
Network and Information Systems (NIS2) |
|
|
ISO 27002:2022 |
Network and Information Systems (NIS2) |
|
| ISO 27002:2022 | ISO 22301:2019 | Download |
| C5:2020 | ISO 27001:2022 and ISO 27002:2022 | Download |
| ISO 27001:2013 | ISO 27001:2022 | Download |
| NIST CSF 1.1 | NIST CSF 2.0 | Download |
Before using them you will need to edit two columns on the CSV file used to tell eramba the name of your compliance packages in eramba.
- Source Compliance Package
- Destination Compliance Package
Playlist
- Episode 1Compliance Mgt Course Intro8 mins left
- Episode 2Problems & Solutions18 mins left
- Episode 3Compliance Management Introduction11 mins left
- Episode 4Using Interface Introduction10 mins left
- Episode 5Basic Access Permissions22 mins left
- Episode 6Compliance Packages12 mins left
- Episode 7Compliance Package Database7 mins left
- Episode 8Policy Management43 mins left
- Episode 9Internal Controls60 mins left
- Episode 10Project Management23 mins left
- Episode 11Exception Management20 mins left
- Episode 12External Audit Findings15 mins left
- Episode 13Dynamic Statuses16 mins left
- Episode 14CSV Imports8 mins left
- Episode 15Reporting15 mins left
- Episode 16Mapping Compliance Packages4 mins left
- Episode 17Compliance Analysis21 mins left
- Episode 18Roll Out20 mins left