Threats & Vulnerabilities
How a database of known vulnerabilities and threats can be used
Introduction
Identifying Threats and Vulnerabilities is common practice in Risk Management, in eramba you can use our pre-built database or simply use a text field to describe them. If you do not want to do this, remember that these fields are optional, so by using Customizations you could remove them from the form.
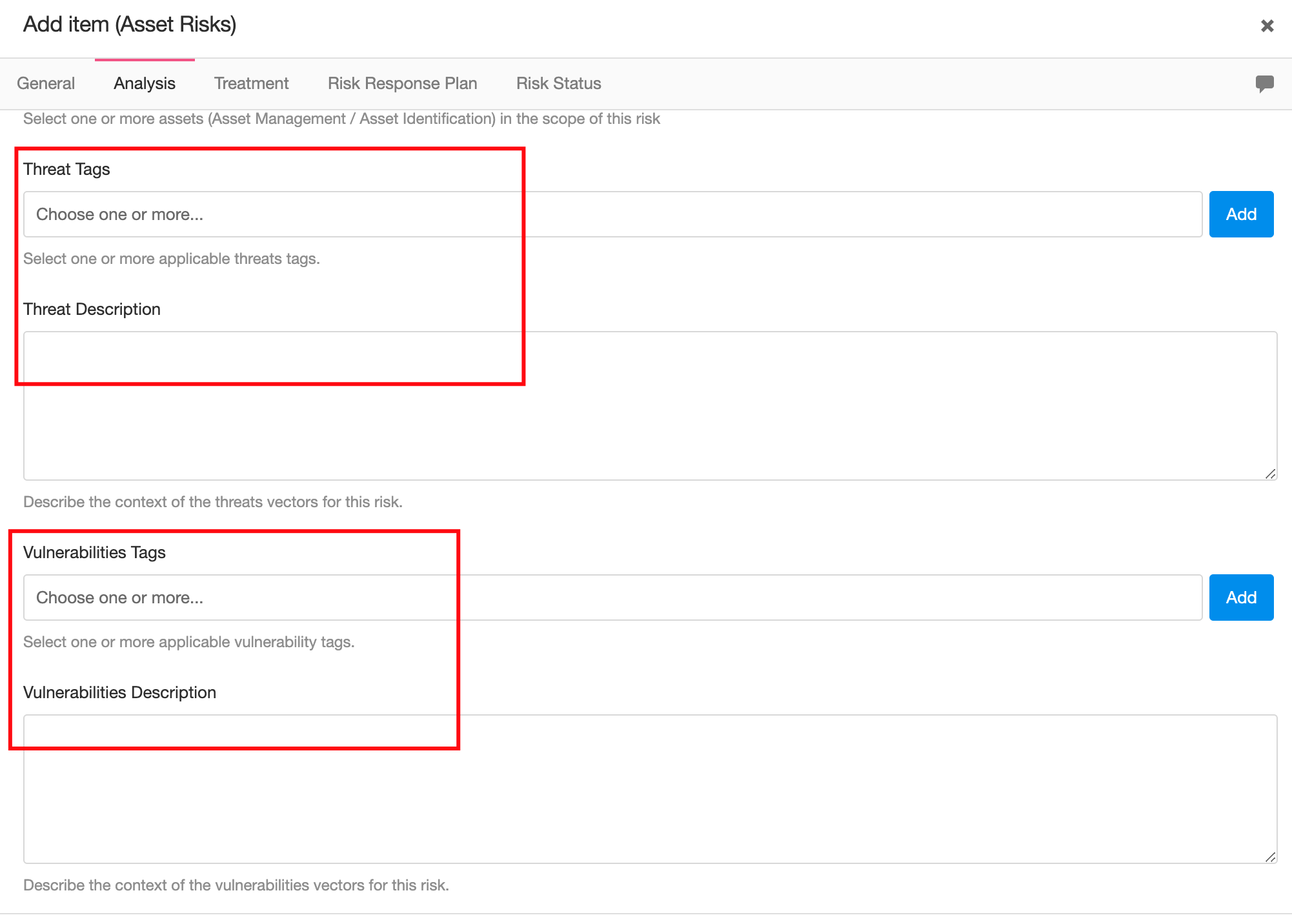
Tags come from a built-in database that can be customised to your needs by removing, adding and renaming threats and vulnerabilities. This database is managed from Settings / Threats and Vulnerabilities.
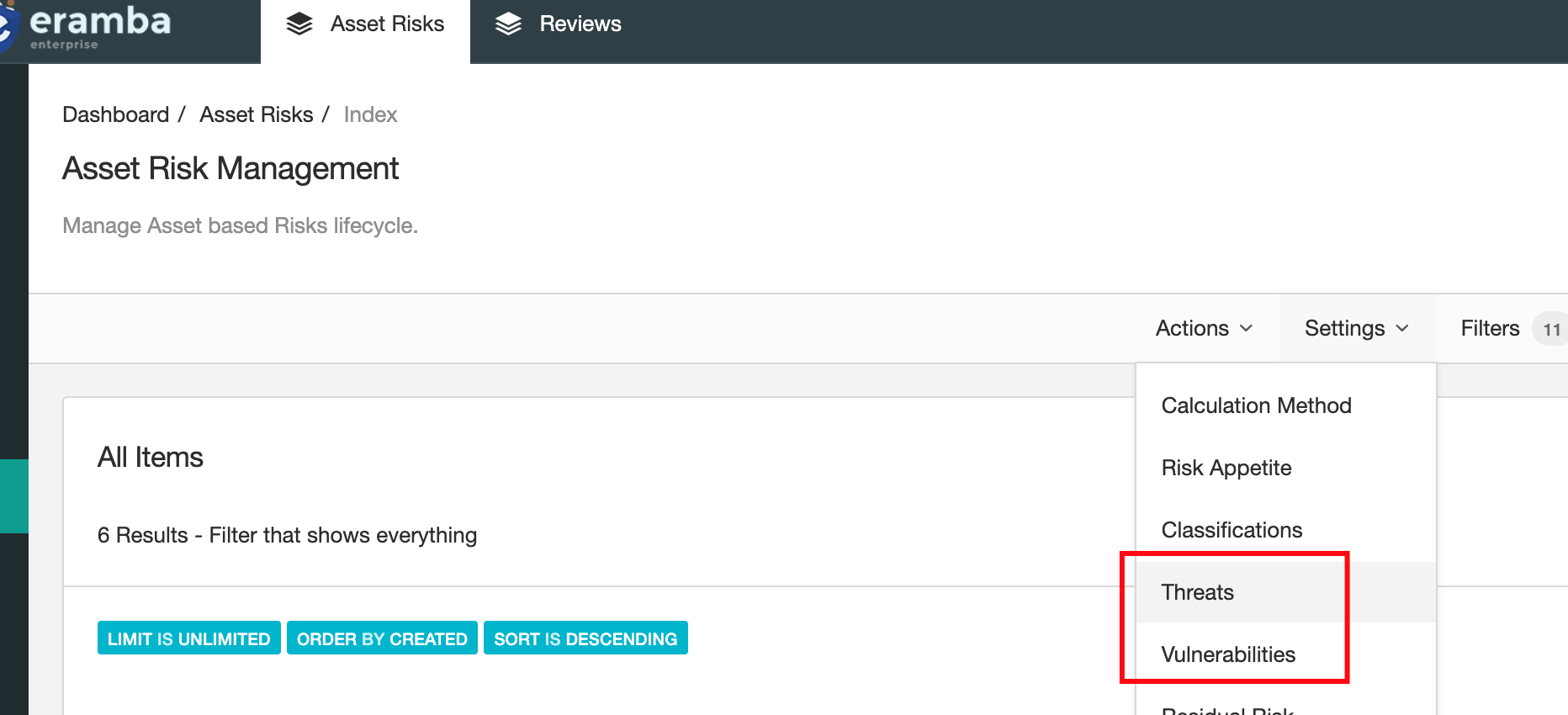
Automatic Suggestion
When using the Asset and Third Party module, at the analysis phase of the Risk creation you will need to asociate Assets with the Risk.
Threats and Vulnerabilities are automatically based on the "Type" of the asset (Software, Data Asset, etc.). These suggestions might not always be accurate and therefore you will have to adjust them. The database that links Threats, Vulnerabilities and their associated Asset Types does not have a user interface.
Managing Database
When accessing the Threats and Vulnerabilities settings, you can see the list of items on the database. Note the relationship between them and Asset Types, this will be used if automatic suggestions are applicable.
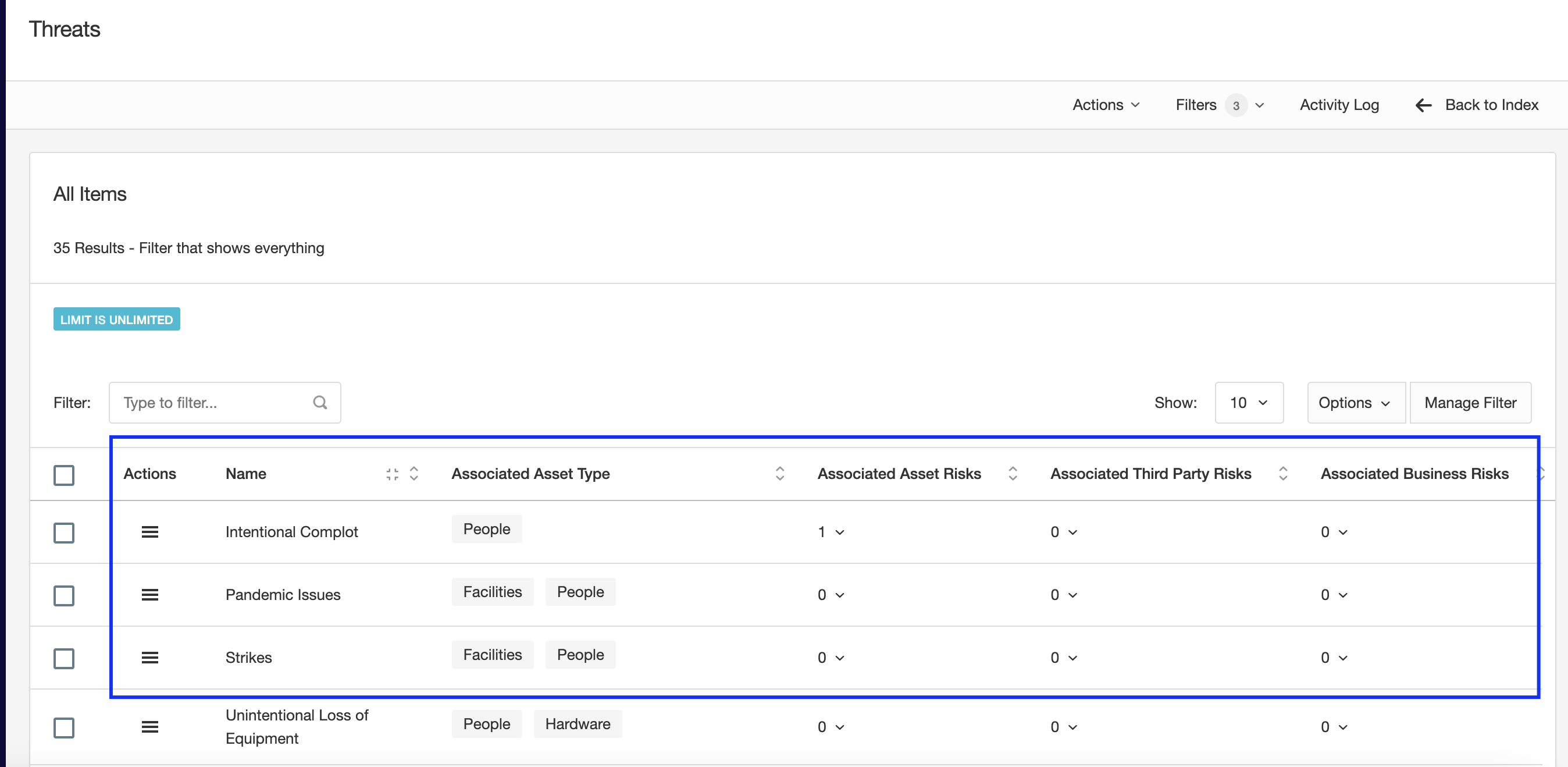
In this interface, you can see which items are used on Risks, and you can edit and delete items as well.
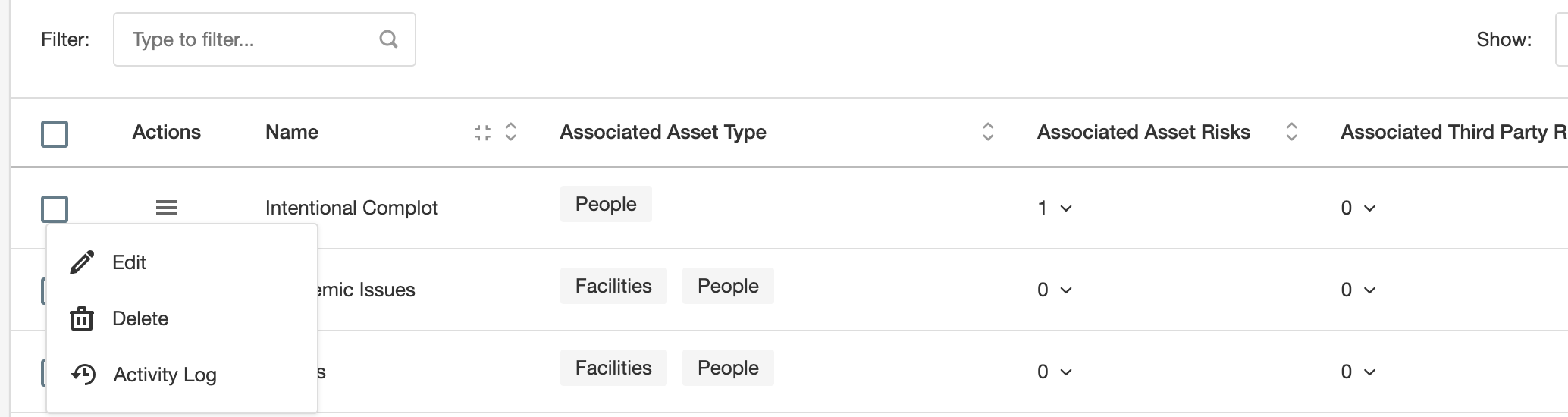
Note that only items not being used can be deleted. If you wish to expand the database with your threats and vulnerabilities, you can use the CSV import functionality.
Playlist
- Episode 1Introduction to Risk Management7 mins left
- Episode 2Problem vs. Solution Principle5 mins left
- Episode 3Typical Risk Questions8 mins left
- Episode 4Risk Calculation Methods4 mins left
- Episode 5Configuring the Risk Module2 mins left
- Episode 6Risk Management Related Modules1 min left
- Episode 7Identifying Risks Inputs7 mins left
- Episode 8Identifying Risk Solutions5 mins left
- Episode 9Creating Risks4 mins left
- Episode 10Threats & Vulnerabilities1 min left
- Episode 11Reviewing Risks7 mins left