Use Cases
Detailed explanation of the different use cases and their checklist
Learning Instructions
The first phase in the implementation roadmap is to define what use cases you will implement in eramba. Based on the use case you choose eramba will give you precise instructions to implement and operate that use case.
On each implementation phase, click on the left panel for your use, read the required courses and implement tasks as indicated.
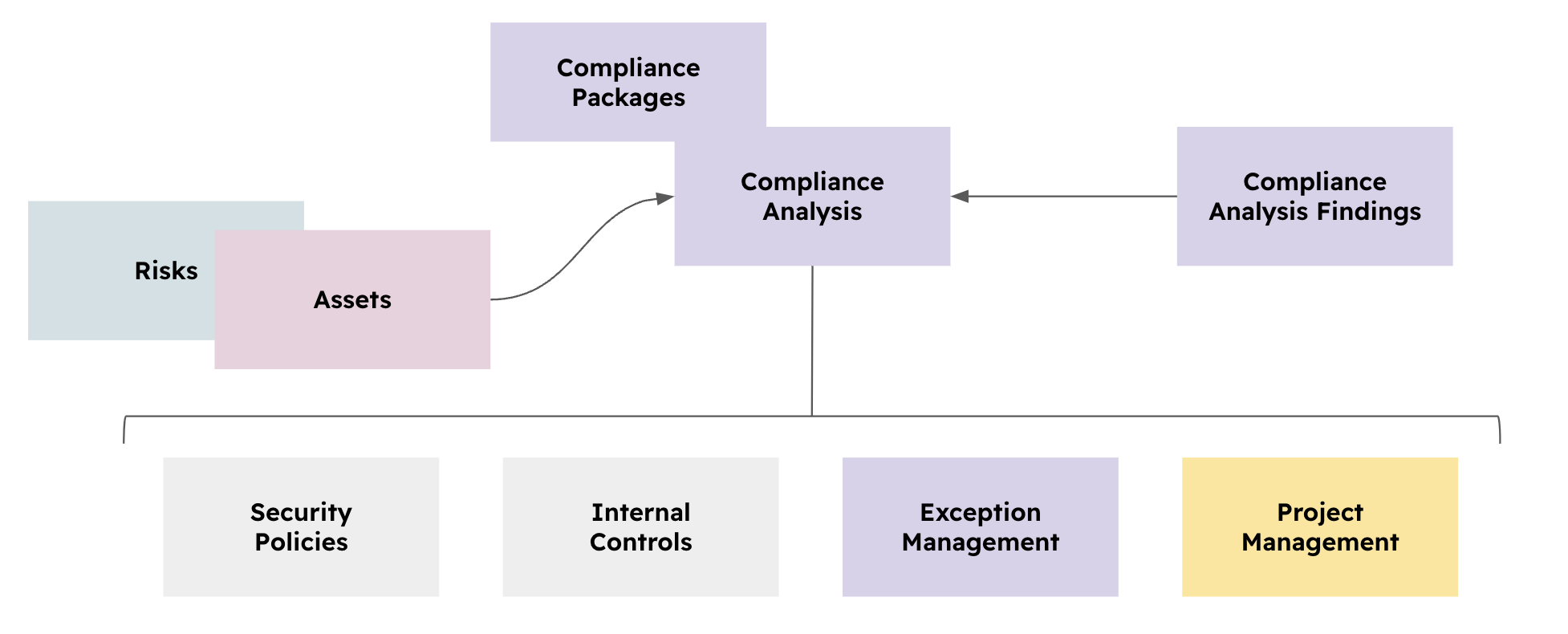
Compliance
The Compliance use case helps organisations with:
- Maintain compliance with ISO, PCI, SOC, NIST, DORA, etc. or specific regulations
- Maintain compliance with their customer-specific compliance requirements
- Tracking external Audit Findings
- Manage Policies and their Reviews
- Manage Internal controls and their Audits
- Manage Exceptions and their Reviews
- Manage Projects and their reviews
This use case requires the following modules:
- Compliance Management / Compliance Packages
- Compliance Management / Compliance Analysis
- Compliance Management / Compliance Exceptions
- Compliance Management / Compliance Analysis Findings
- Controls Catalogue / Internal Controls
- Controls Catalogue / Security Policies
- Security Operations / Project Management
The diagram below shows how these basic relations interact one with another.
Risk Management
The Risk Management use case helps organisations with:
- Building and maintaining a Risk Register
- Track Risk ownership and treatment
- ISO, etc compatible Risk Frameworks
- Manage Policies and their Reviews
- Manage Internal controls and their Audits
- Manage Exceptions and their Reviews
- Manage Projects and their reviews
- Manage Continuity Plans
This use case requires the following modules:
- Organization / Business Units
- Organization / Business Units / Process
- Organization / Third Parties
- Organization / Liabilities
- Asset Management / Assets
- Risk Management / Asset Risk Management
- Risk Management / Third Party Risk Management
- Risk Management / Business Impact Analysis
- Risk Management / Risk Exceptions
- Controls Catalogue / Internal Controls
- Controls Catalogue / Security Policies
- Security Operations / Project Management
The diagram below shows how these basic relations interact one with another.

Data Privacy
The Compliance use case helps organisations with:
- Understand how data moves around and how is protected
- Deal with GDPR and related regulations
- Manage Policies and their Reviews
- Manage Internal controls and their Audits
- Manage Exceptions and their Reviews
- Manage Projects and their reviews
This use case requires the following modules:
- Organization / Business Units
- Organization / Third Parties
- Organization / Liabilities
- Asset Management / Assets
- Asset Management / Data Flows
- Risk Management / Asset Risk Management
- Risk Management / Third Party Risk Management
- Risk Management / Business Impact Analysis
- Controls Catalogue / Internal Controls
- Controls Catalogue / Security Policies
- Security Operations / Project Management
The diagram below shows how these basic relations interact one with another.

Incident Management
The Incident Management use case helps organisations with:
- Keeping track of their Incidents
- Associate incidents with well-known Risks
- Systematically analyse Incidents
This use case requires the following modules:
The Incident Management use case requires the following modules:
- Security Operations / Incident Management
Optionally:
- Asset Management / Assets
- Controls Catalogue / Internal Controls
- Controls Catalogue / Security Policies
- Risk Management / Asset Risk Management
- Risk Management / Third Party Risk Management
- Risk Management / Business Impact Analysis
The diagram below shows how these basic relations interact one with another.

Awareness Programs
The Awareness Program use case helps organisations with:
- Distribute awareness content (videos, disclaimer texts, etc) to audience inside and outside the organisation
- Comply with common standards in the Awareness space
- Track awareness of policies
This use case requires the following modules:
- Security Operations / Awareness Programs
Optionally:
- Controls Catalogue / Security Policies
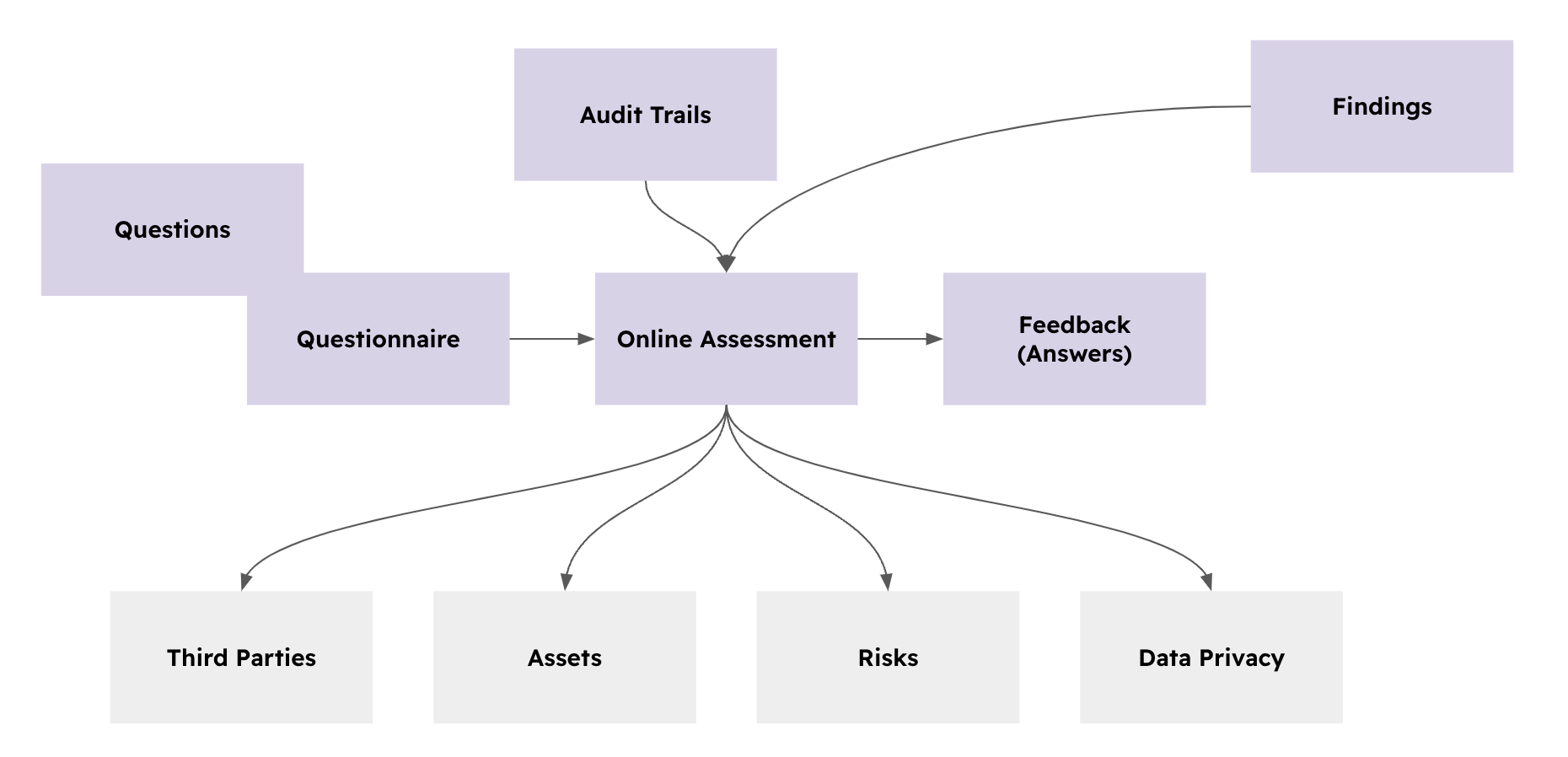
Online Assessments
The Online Assessment use case helps organisations with:
- Distributing online questionnaires
- Assess suppliers using an online platform
- Perform Risk, Privacy, etc Identification exercises
- Keep track of compliant and non-compliant suppliers
This use case requires the following modules:
- Compliance Management / Online Assessments
Optionally:
- Organisation / Third Parties
- Risk Management / Asset Risk Management
- Risk Management / Third Party Risk Management
- Risk Management / Business Impact Analysis
- Asset Management / Data Privacy
The diagram below shows how these basic relations interact one with another.
Account Reviews
The Account Review module use case helps organisations with:
- Automatically Review Accounts from Systems
- Supports: LDAP, AWS and Custom Applications
- Allows you to assign Account Reviews to teams or individuals
- Document Findings when accounts are found to be bugus
This use case requires the following modules:
- Security Operations / Account Reviews
- Optional: System / Settings / LDAP Connectors
Playlist
- Episode 1The Journey2 mins left
- Episode 2Phases2 mins left
- Episode 3Use Cases5 mins left
- Episode 4Installation or SaaS0 mins left
- Episode 5Access Management5 mins left
- Episode 6Customization5 mins left
- Episode 7Data Entry3 mins left
- Episode 8Reporting1 min left
- Episode 9Automation2 mins left
- Episode 10Rollout3 mins left